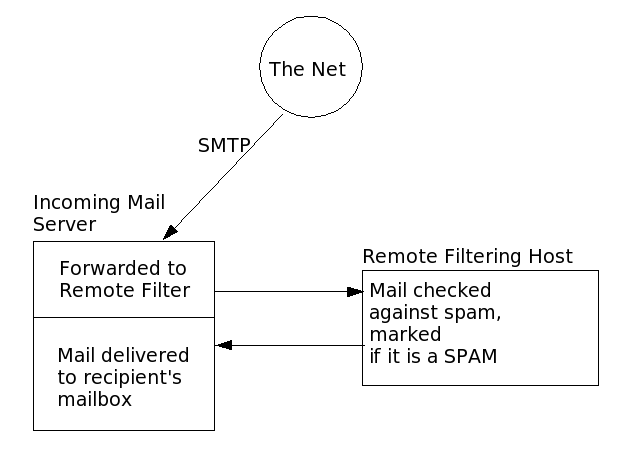
Again,
every single byte is significant. What this alias does is: It
redirects all incoming mail to the command
/usr/bin/spamc -t
10 | /usr/share/spamassassin/filter.pl
which
runs the spamassassin client
(spamc) with a timeout of 10 seconds
and redirects its output to our filter.pl
Perl script installed under
/usr/share/spamassassin.
I've configured spamassassin so that it prefixes the subject of a spam
message with "***SPAM***".
Furthermore, if spamassassin decides that an
email is SPAM, it inserts a header which reads: "X-Spam-Flag: YES".
The Perl script "filter.pl" parses the output of the "spamc" command;
finds out the real recipient and sender of the message; reorgani[sz]es
the headers (prepends "X-" to most header lines so that the SMTP
server doesn't detect a mail loop) and sends its back to the original
recipient.
The filter.pl
program
This is a simple Perl
script which
parses the output of spamc
(the spamassassin client) to find who the sender and recipient of
the original message were; modify the original headers by prepending
"X-" and resending the spamc output the original recipient. Note that
modifying the original headers is crucial; otherwise SMTP servers
will detect email loops; i.e. messages bouncing between two addresses
indefinitely.
Like all well
behaving UNIX programs,
filter.pl
logs its actions to
syslog. You can see what this program has logged using the
command:
grep
SPAM-FILTER /var/log/syslog
Installing
filter.pl
This step is very
easy. Just download filter.pl;
save and move it to
/usr/share/spamassassin/filter.pl;
set it world executable and owned by root. (A more detailed install
procedure is described in the script itself.)
chown root:root
/usr/share/spamassassin/filter.pl
chmod a+x
/usr/share/spamassassin/filter.pl
Helping your
users setting up their .forward and .procmailrc files
We use two simple
shell scripts that we
have installed in /usr/local/bin
and we tell our users (who want to have their mail checked against
spam) to login to their regular accounts and execute the "start_filtering"
command. This shell script checks whether they already have any .forward or .procmailrc
files in their homes; and creates both files if it is appropriate. They
can issue the "stop_filtering"
command anytime they want to resume learning more about enlargement of
various parts of the human body.
#!/usr/bin/sh
###################
# start_filtering #
###################
# This script is a supplement of Remote-SPAM-Filtering
#
# Setting up Remote SPAM Filtering requires the users
# to place two mail delivery related dot files in their
# home directories.
#
# These files are .forward and .procmailrc
#
# by: Can Ugur Ayfer - Bilkent University
# May 2004
######################################################
# There should be no .forward .procmailrc files
# in the home dir
#
if test -f "$HOME/.forward"; then
echo " "
echo "You already have a .forward file in your home
directory."
echo "The .forward file contains the line(s):"
echo " "
cat $HOME/.forward
echo " "
echo "We CANNOT enable spam filtering for this account."
echo " "
exit 1
fi
if test -f "$HOME/.procmailrc"; then
echo " "
echo "You already have a .procmailrc file in your home
directory."
echo "The .procmailrc file contains the line(s):"
echo " "
cat $HOME/.procmailrc
echo " "
echo "We CANNOT enable spam filtering for this account."
echo " "
exit 1
fi
#
# create .forward and .procmailrc files
cat > $HOME/.forward << __EOF__
"|IFS=' ' && exec /usr/bin/procmail -f- || exit 75 #user"
__EOF__
chmod 600 $HOME/.forward
cat > $HOME/.procmailrc << __EOF__
:0
* ^X-Filter.*Bilkent
\$DEFAULT
:0
* < 256000
! filter@nospam.bilkent.edu.tr
:0
\$DEFAULT
__EOF__
chmod 600 $HOME/.procmailrc
echo " "
echo " SPAM checking is now ENABLED for your account. "
echo " "
echo " Please send yourself an e-mail to make sure that "
echo " the setup is working fine."
echo " If you believe that there is a problem"
echo " with your incoming mail, please issue"
echo " the stop_filtering command to undo the changes."
echo " "
echo " Any mail that the scanner software believes"
echo " to be a spam, will be marked with *****SPAM*****"
echo " in the subject line and sent as a regular"
echo " mail to your mailbox. "
echo " "
echo " If you believe the spam scanner works fine,"
echo " you can set your e-mail program's filters"
echo " so that all marked messages are sent to Trash"
echo " automatically."
echo " "
|
#!/usr/bin/sh
###################
# stop_filtering #
###################
#
# This script is a
supplement of Remote-SPAM-Filtering
#
# Disabling Remote SPAM
Filtering requires the users
# to remove the two mail
delivery related dot files in their
# home directories.
#
# These files are .forward
and .procmailrc
#
# by: Can Ugur Ayfer -
Bilkent University
#
May 2004
######################################################
#
# There should be a
.forward and a .procmailrc file in the home dir
if [ -f
$HOME/.forward -a -f $HOME/.procmailrc ]
then
echo " "
echo ".forward
file contains:"
cat
$HOME/.forward
echo " "
echo " "
echo
".procmailrc file contains:"
cat
$HOME/.procmailrc
echo " "
echo "Are you
sure that you want to delete these two files? (y/N): "
read ANS
case $ANS in
[yY])
/bin/rm $HOME/.procmailrc
/bin/rm $HOME/.forward
echo " "
echo "Your .procmailrc and .forward files are now deleted."
echo "Spam checking is now disabled for your account."
echo " "
echo "You can enable spam checking by issuing the command
\"start_filtering\""
echo " "
exit;;
esac
echo " "
echo "Nothing
changed."
echo " "
exit
fi
echo " "
echo
" You do not have a .forward or .procmailrc
file!"
echo
" This means your account is NOT set for spam
checking."
echo
" There is no sense trying to stop spam
checking for this account!"
|
May 2004